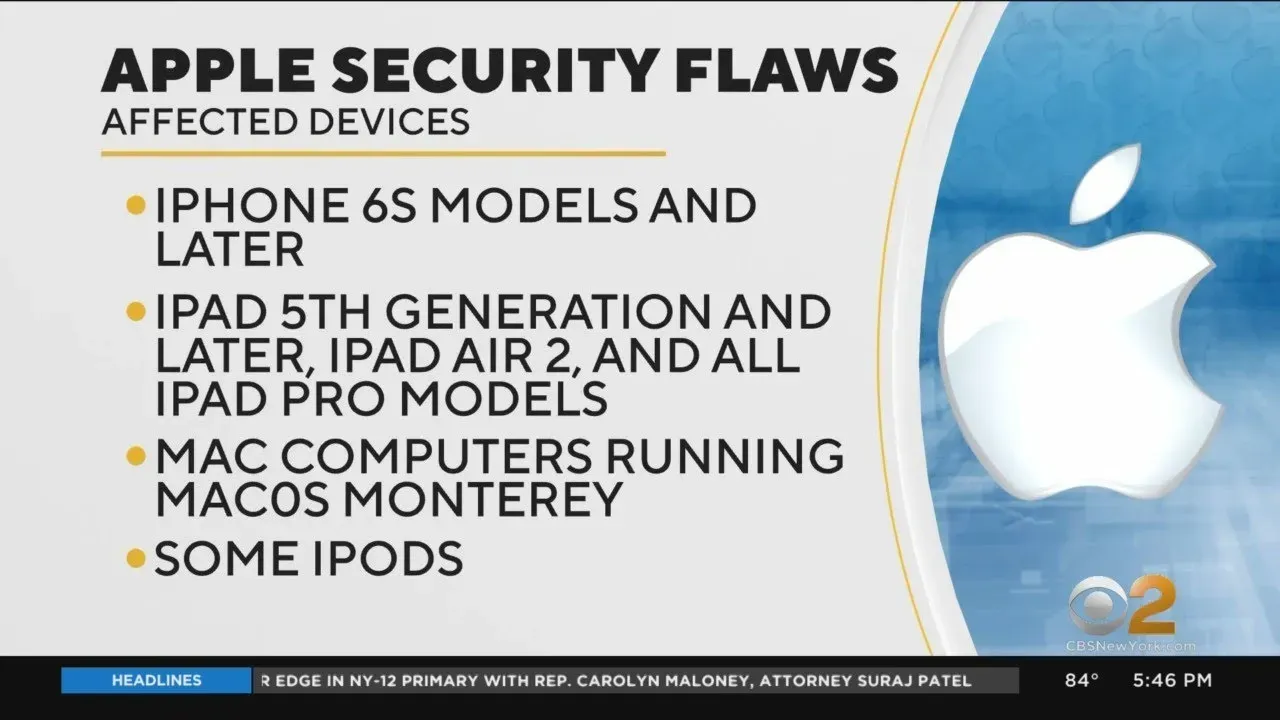
The recent discovery of an Apple security flaw has raised significant concerns among users of its devices, particularly affecting iPhones and MacBooks. This vulnerability, linked to a specific set of A- and M-series chips, could potentially expose sensitive information such as emails, location data, and credit card details to unauthorized access. Dubbed a ‘Side-channel attack,’ this breach is particularly alarming as it can occur during routine web browsing activities. Experts have confirmed that the flaw impacts various models, including all iPhone models from 2021 onwards and MacBook Pro and Air models released from 2022. While Apple is aware of the issue and is working on a solution, users are advised to remain vigilant about their data protection in the meantime.
A newly identified vulnerability within Apple’s ecosystem has sparked discussions around device security, especially concerning the iPhone and MacBook lines. This flaw, which has been characterized as a potential iPhone security breach, allows hackers to exploit weaknesses in Apple’s A-series chips, opening the door to unauthorized access to personal data. The implications of this MacBook vulnerability are extensive, potentially compromising user privacy during everyday online activities. As cybersecurity threats evolve, the necessity for robust data protection measures from Apple becomes increasingly apparent. With the ongoing threat of side-channel attacks, users are encouraged to stay informed about their devices’ security status and any forthcoming updates from Apple.
Understanding the Apple Security Flaw
Recent findings have revealed a significant security flaw affecting Apple’s A- and M-series chips, which are integral to devices like iPhones and MacBooks. This vulnerability is characterized as a ‘Side-channel’ attack, enabling hackers to potentially access sensitive user data remotely. The implications of such a breach are concerning, as personal information, including location data, email contents, and payment details, could be exposed during routine web browsing.
Apple has acknowledged this issue and is working swiftly to implement security updates to mitigate the risk. Although the company has stated that the flaw does not pose an immediate threat, users should remain vigilant. As the tech giant rolls out patches, understanding how these vulnerabilities work is crucial for users who prioritize data protection and security on their devices.
Impact on iPhone Security and User Data
The recent security breach affecting iPhones has raised alarms among users who rely heavily on their devices for communication and financial transactions. With the possibility of unauthorized access to sensitive information, the ramifications could be severe. Users are advised to enhance their security measures, such as enabling two-factor authentication and regularly updating their software, to protect against potential threats.
Moreover, as iPhone security breaches become more prevalent, it is essential for Apple to maintain transparency with its users about the risks associated with its devices. The ongoing updates and patches are a step in the right direction, but educating users about safe browsing practices and the importance of data protection is equally vital in combating these vulnerabilities.
MacBook Vulnerability: What You Need to Know
The recent discovery of a security flaw in MacBook models has raised concerns about the overall vulnerability of Apple devices. The flaw affects all MacBook Air and Pro models released from 2022 onwards, indicating that a significant number of users could be at risk. This vulnerability allows hackers to exploit the system and gain access to confidential information, which is particularly alarming given the increasing number of cyberattacks targeting personal data.
As Apple works on a fix, it is crucial for MacBook users to stay informed about the nature of this vulnerability. Understanding how the Side-channel attack operates can empower users to adopt better security practices. Regularly updating your operating system and software can help shield against potential exploits while waiting for Apple’s official patch.
The Importance of Data Protection in Apple Devices
With the growing reliance on technology, data protection has never been more critical, especially for Apple users. The recent vulnerabilities in iPhones and MacBooks underscore the need for robust security measures to safeguard personal information. Apple’s commitment to addressing these flaws is essential, but users must also take proactive steps to protect their data.
Implementing strong passwords, utilizing encryption, and being cautious with third-party applications can significantly enhance data security. As Apple continues to innovate, the responsibility of maintaining security extends beyond the company to each individual user, making data protection a shared priority.
Side-Channel Attacks: A New Threat Landscape
Side-channel attacks represent a sophisticated method that hackers can employ to bypass traditional security measures. This type of attack exploits physical leaks from hardware components, allowing unauthorized access to sensitive information without directly compromising the software. The recent discovery of such an attack on Apple’s chips highlights a pressing need for enhanced security protocols in hardware design.
As researchers continue to analyze the implications of these attacks, Apple must not only focus on immediate fixes but also invest in long-term solutions to prevent future vulnerabilities. This may involve redesigning their chips or implementing new encryption techniques that can withstand such sophisticated breaches.
Addressing the Apple A-Series Chip Issue
The A-series chips, which power many Apple devices, are renowned for their performance and efficiency. However, the recent security flaw reveals that even the most advanced technology can have weaknesses. The vulnerability identified in these chips could potentially expose users to data breaches, making it imperative for Apple to address these issues swiftly and effectively.
In light of this situation, users of devices equipped with A-series chips should remain alert for updates from Apple regarding security patches. Additionally, they should consider utilizing additional security software that can provide an extra layer of protection against potential exploits.
Steps Apple is Taking to Fix the Vulnerability
In response to the identified security flaw, Apple has committed to releasing updates aimed at patching the vulnerabilities in its devices. The company is working closely with cybersecurity experts to ensure that the updates effectively mitigate the risks posed by the Side-channel attack. Users can expect these updates to be rolled out in a timely manner, as Apple prioritizes user security.
Additionally, Apple is likely to enhance its internal security protocols to prevent similar vulnerabilities from emerging in the future. This proactive approach is essential in maintaining user trust and safeguarding personal data against increasingly sophisticated cyber threats.
User Awareness and Education on Security Practices
As Apple addresses the security flaws in its devices, user awareness plays a crucial role in enhancing data protection. Users should educate themselves about potential threats and the importance of implementing best security practices. This includes regularly updating devices, understanding phishing scams, and being cautious when downloading applications from unknown sources.
Moreover, Apple can aid in this effort by providing clear and accessible information about security features and practices. By fostering an informed user base, Apple can create a more resilient community that is better prepared to handle the evolving landscape of cyber threats.
The Future of Apple Security Protocols
The recent security flaws have prompted discussions about the future of security protocols within Apple’s ecosystem. As technology continues to advance, so too must the measures in place to protect user data. It is likely that Apple will invest more in research and development focused on security innovations, potentially leading to the creation of new chip designs that are inherently more secure.
Furthermore, as cyber threats become more sophisticated, Apple may also collaborate with other tech companies and cybersecurity firms to establish industry-wide standards for data protection. By leading the charge in enhancing security measures, Apple can set a precedent for the tech industry as a whole.
Frequently Asked Questions
What is the Apple security flaw affecting iPhones and MacBooks?
The Apple security flaw refers to a recently discovered vulnerability in Apple’s A- and M-series chips that allows hackers to perform a side-channel attack. This type of attack can enable unauthorized remote access to sensitive user data, including email, location, and credit card information.
How does the iPhone security breach occur?
The iPhone security breach occurs through a side-channel attack that takes advantage of the security flaw in Apple’s chips. This vulnerability can be exploited while users are browsing the web, allowing hackers to access personal data without the user’s consent.
What devices are affected by the MacBook vulnerability?
The MacBook vulnerability affects all MacBook Air and Pro models from 2022 onwards, as well as Mac mini, iMac, Mac Studio, and Mac Pro models from 2023 onwards. This also extends to all iPad Pro, Air, and mini models from 2021 and all iPhones from 2021.
What steps is Apple taking to address the data protection issue?
Apple has acknowledged the security flaw and has been notified by researchers. The company is working on a fix to address the data protection issue and plans to implement it soon to safeguard users against potential exploits.
Are there any immediate risks associated with the Apple A-series chip issue?
According to Apple, the Apple A-series chip issue does not pose an immediate risk to users. However, the company is prioritizing a solution to ensure the safety and security of user data.
What is a side-channel attack in relation to Apple devices?
A side-channel attack is a method used by hackers to gain unauthorized access to data by exploiting the physical implementation of a system, rather than the software itself. In the context of Apple devices, this attack utilizes a security flaw in the A- and M-series chips, potentially compromising user information.
How can users protect their data until the Apple security flaw is fixed?
To protect their data until the Apple security flaw is addressed, users should keep their operating systems updated, avoid clicking on suspicious links, and consider using additional security measures, such as VPNs and security software, while browsing.
| Device Type | Models Affected | Impact of Security Flaw | Expected Fix |
|---|---|---|---|
| iPhone | All iPhones from 2021 onwards | Unauthorized access to email, location, and credit card information | Fix expected soon after notification to Apple |
| iPad | All iPad Pro, Air, and mini models from 2021 onwards | Unauthorized access to email, location, and credit card information | Fix expected soon after notification to Apple |
| MacBook | All MacBook Air and Pro models from 2022 onwards | Unauthorized access to email, location, and credit card information | Fix expected soon after notification to Apple |
| Mac | All Mac mini, iMac, Mac Studio, and Mac Pro models from 2023 onwards | Unauthorized access to email, location, and credit card information | Fix expected soon after notification to Apple |
Summary
The Apple security flaw presents a significant concern for users of its devices, including the iPhone, iPad, and MacBook. This vulnerability allows hackers to potentially access sensitive user data remotely, which raises alarms about privacy and data security. Although Apple has stated that the flaw does not pose an immediate risk, it is crucial for users to remain vigilant and await the upcoming fixes that the company is expected to implement. Staying updated on security patches and being aware of device vulnerabilities is essential for maintaining digital security.